环境描述 主DNS维护三个view:
三个view均包含了域aaaa.com的信息,现在需要将主DNS上的aaaa.com域信息分别对应地传输到从DNS上。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 +-------------------+ +-------------------+ | 主DNS | ---\ | 从DNS | | (192.168.18.143) | ---/ | (192.168.18.144) | +-------------------+ +-------------------+ | +-------------------+ +-------------------+ | "aaaa.com" | ---\ | "aaaa.com" | | in view "user1" | ---/ | in view "user1" | +-------------------+ +-------------------+ | | +-------------------+ +-------------------+ | "aaaa.com" | ---\ | "aaaa.com" | | in view "user2" | ---/ | in view "user2" | +-------------------+ +-------------------+ | | +-------------------+ +-------------------+ | "aaaa.com" | ---\ | "aaaa.com" | | in view "default" | ---/ | in view "default" | +-------------------+ +-------------------+
1 2 3 4 5 6 7 8 9 10 11 12 13 14 $TTL 600@ IN SOA dns1.aaaa.com. aaaa.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 @ NS dns2 @ NS dns3 dns1 A 192.168.18.143 dns2 A 192.168.18.144 dns3 A 192.168.18.145 user A 192.168.18.144
1 2 3 4 5 6 7 8 9 10 11 12 13 14 $TTL 600@ IN SOA dns1.aaaa.com. aaaa.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 @ NS dns2 @ NS dns3 dns1 A 192.168.18.143 dns2 A 192.168.18.144 dns3 A 192.168.18.145 user A 192.168.18.145
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 $TTL 600@ IN SOA dns1.aaaa.com. aaaa.com. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 @ NS dns2 @ NS dns3 dns1 A 192.168.18.143 dns2 A 192.168.18.144 dns3 A 192.168.18.145 user A 192.168.18.144 user A 192.168.18.145
主从侧DNS配置 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 key "user1key" { algorithm hmac-md5; secret "yJlkV++JGsTTkvdZJHO2ww==" ; }; key "user2key" { algorithm hmac-md5; secret "QZUrG/ATFi9GlPvOoQF15w==" ; }; key "defaultkey" { algorithm hmac-md5; secret "vezhpYBM2goIYIV71BK4lQ==" ; }; view "user1" { match-clients { key user1key; }; recursion no; allow-transfer { key user1key; }; server 192.168.18.144 { keys user1key; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type master; file "aaaa.com.user1" ; }; }; view "user2" { match-clients { key user2key; }; recursion no; allow-transfer { key user2key; }; server 192.168.18.144 { keys user2key; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type master; file "aaaa.com.user2" ; }; }; view "default" { match-clients { key defaultkey; }; recursion no; allow-transfer { key defaultkey; }; server 192.168.18.144 { keys defaultkey; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type master; file "aaaa.com.default" ; }; };
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 key "user1key" { algorithm hmac-md5; secret "yJlkV++JGsTTkvdZJHO2ww==" ; }; key "user2key" { algorithm hmac-md5; secret "QZUrG/ATFi9GlPvOoQF15w==" ; }; key "defaultkey" { algorithm hmac-md5; secret "vezhpYBM2goIYIV71BK4lQ==" ; }; view "user1" { match-clients { key user1key; }; recursion no; allow-transfer { 192.168.18.144; }; server 192.168.18.143 { keys user1key; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type slave; masters { 192.168.18.143; }; file "aaaa.com.user1" ; }; }; view "user2" { match-clients { key user2key; }; recursion no; allow-transfer { 192.168.18.144; }; server 192.168.18.143 { keys user2key; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type slave; masters { 192.168.18.143; }; file "aaaa.com.user2" ; }; }; view "default" { match-clients { key defaultkey; }; recursion no; allow-transfer { 192.168.18.144; }; server 192.168.18.143 { keys defaultkey; }; zone "." { type hint; file "named.ca" ; }; zone "aaaa.com" { type slave; masters { 192.168.18.143; }; file "aaaa.com.default" ; }; };
验证 验证步骤:
启动主从DNS服务;
在192.168.18.143上,将DNS解析地址设置为192.168.18.143,使用user1key获取aaaa.com的AXFR数据:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [root@dns1 ~] ; <<>> DiG 9.12.2 <<>> -k user1key.key @192.168.18.143 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.144 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 user1key. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532510827 300 16 XqpgMtmXOKCwjrvSCRB+ew== 5171 NOERROR 0 ;; Query time: 0 msec ;; SERVER: 192.168.18.143 ;; WHEN: Wed Jul 25 05:27:07 EDT 2018 ;; XFR size: 9 records (messages 1, bytes 341)
在192.168.18.143上,将DNS解析地址设置为192.168.18.143,使用user2key获取aaaa.com的AXFR数据:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [root@dns1 ~] ; <<>> DiG 9.12.2 <<>> -k user2key.key @192.168.18.143 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.145 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 user2key. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532510936 300 16 U5m0brG5j7a6JHSitc4g2A== 30892 NOERROR 0 ;; Query time: 1 msec ;; SERVER: 192.168.18.143 ;; WHEN: Wed Jul 25 05:28:56 EDT 2018 ;; XFR size: 9 records (messages 1, bytes 341)
在192.168.18.143上,将DNS解析地址设置为192.168.18.143,使用defaultkey获取aaaa.com的AXFR数据:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [root@dns1 ~]# dig -k defaultkey.key @192.168.18.143 aaaa.com. AXFR ; <<>> DiG 9.12.2 <<>> -k defaultkey.key @192.168.18.143 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.144 user.aaaa.com. 600 IN A 192.168.18.145 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 defaultkey. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532511138 300 16 5tx+79oaE18eT+NvXf1rkw== 54983 NOERROR 0 ;; Query time: 0 msec ;; SERVER: 192.168.18.143#53(192.168.18.143) ;; WHEN: Wed Jul 25 05:32:18 EDT 2018 ;; XFR size: 10 records (messages 1, bytes 359)
可见在主DNS上可以通过TSIGKEY来获取对应的域信息。现在192.168.18.144上的启动从DNS服务器。
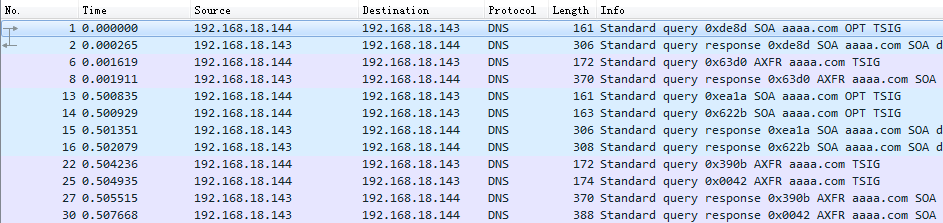
在主DNS上抓取到notify及axfr的报文:
可见aaaa.com传输了三次,对应三个view。而且每次传输过程中都带了TSIGKEY。
在192.168.18.144上重复上述2、3、4步骤,但是将解析地址换为192.168.18.144,得到的结果分别为:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [root@dns2 ~] ; <<>> DiG 9.12.2 <<>> -k user1key.key @192.168.18.144 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.144 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 user1key. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532511856 300 16 AtOUZtJp8LaVJ9kjADomCg== 19175 NOERROR 0 ;; Query time: 1 msec ;; SERVER: 192.168.18.144 ;; WHEN: Wed Jul 25 05:44:16 EDT 2018 ;; XFR size: 9 records (messages 1, bytes 341)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 [root@dns2 ~] ; <<>> DiG 9.12.2 <<>> -k user2key.key @192.168.18.144 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.145 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 user2key. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532511904 300 16 mmQlhV7XoNC1eIzRaT/g4w== 9729 NOERROR 0 ;; Query time: 1 msec ;; SERVER: 192.168.18.144 ;; WHEN: Wed Jul 25 05:45:04 EDT 2018 ;; XFR size: 9 records (messages 1, bytes 341)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [root@dns2 ~] ; <<>> DiG 9.12.2 <<>> -k defaultkey.key @192.168.18.144 aaaa.com. AXFR ; (1 server found) ;; global options: +cmd aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 aaaa.com. 600 IN NS dns1.aaaa.com. aaaa.com. 600 IN NS dns2.aaaa.com. aaaa.com. 600 IN NS dns3.aaaa.com. dns1.aaaa.com. 600 IN A 192.168.18.143 dns2.aaaa.com. 600 IN A 192.168.18.144 dns3.aaaa.com. 600 IN A 192.168.18.145 user.aaaa.com. 600 IN A 192.168.18.144 user.aaaa.com. 600 IN A 192.168.18.145 aaaa.com. 600 IN SOA dns1.aaaa.com. aaaa.com. 0 86400 3600 604800 10800 defaultkey. 0 ANY TSIG hmac-md5.sig-alg.reg.int. 1532511935 300 16 mAi9a/NVux/+qY/Le2DJYw== 47741 NOERROR 0 ;; Query time: 1 msec ;; SERVER: 192.168.18.144 ;; WHEN: Wed Jul 25 05:45:35 EDT 2018 ;; XFR size: 10 records (messages 1, bytes 359)
在从DNS验证了三个view中的aaaa.com域信息与主DNS上保持一致。